Block it.

Image by ndemello from Pixabay
There have been times, were there was no answer, when the question was raised: “how can I block access to certain internet domains in the modern workplace scenario?”
Those times are over.
With Network Protection, Microsoft Defender ATP (MDATP) and Microsoft Cloud App Security (MCAS), we now have multiple possibilities to block websites.
The cool thing about Network Protection: -as the name implies- it sits in the Windows 10 network layer. With that said, it blocks internet connections from any browser and from any other application!
Network Protection can be turned on in multiple ways, including Intune and PowerShell.
Blocking Single Domains or IP Addresses
First, you can manually add a custom indicator in MDATP under Settings/Indicators to block certain Domains. If you do not ‘enable’ Network Protection on your clients – this takes only effect in Edge.

After clicking on the ‘add indicator’ button, you will have to specify the URL …
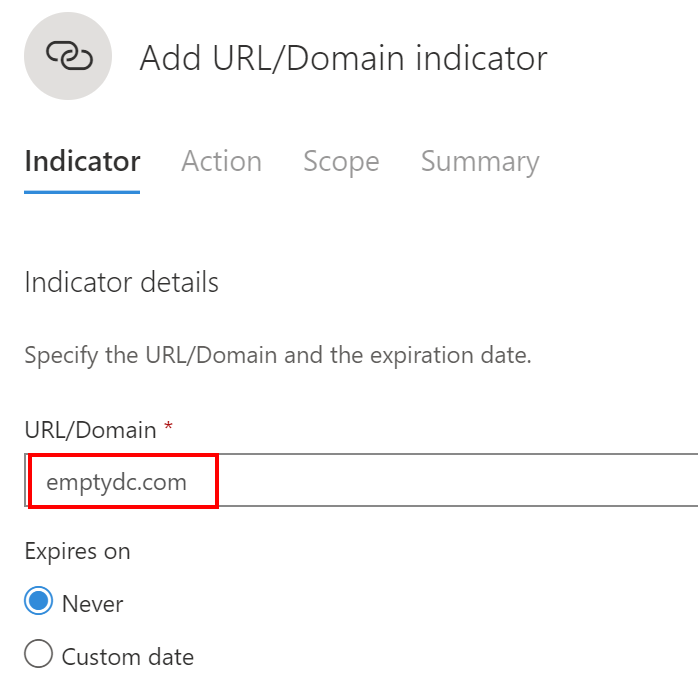
… and let MDATP know, if you just want to get alerted or if you want to block the access:
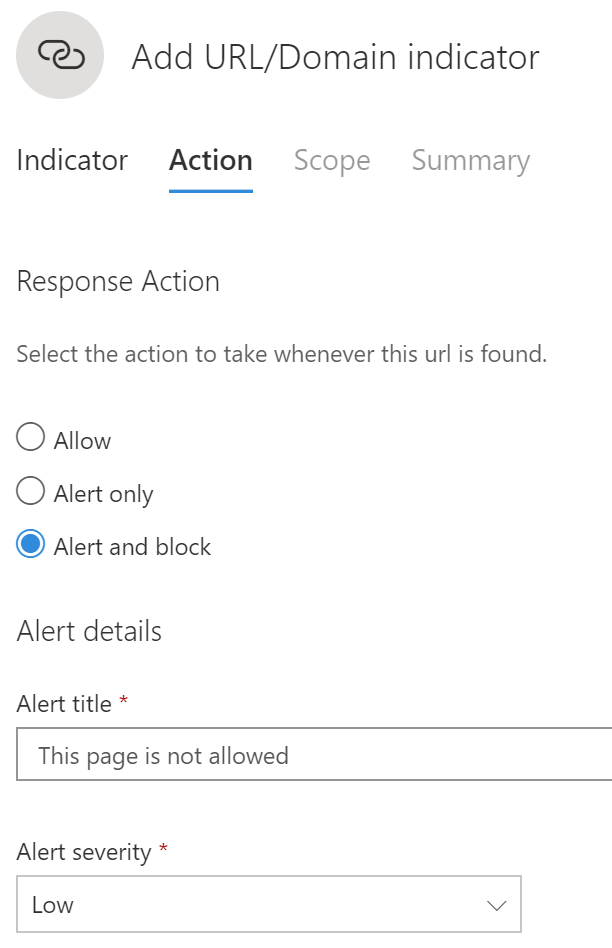
You don’t have to apply this to your whole environment – you can specify a target machine group:

You just saw the fundamental technique of everything we will talk about in the rest of this article. The only difference in the upcoming topics is the way how indicators are created. We just created them manually, now I will show you how to create them automatically based on other information (even though they will not always be visible to you).
As you have seen, when configuring custom indicators, we need to know exactly which URL we want to block. In other situations, people don’t exactly know the URL of the websites they need to block, but only the category. This is where content filtering comes into play.
Blocking based on Content
This is a new feature in MDATP – as announced at Ignite 2019. To turn this on, go to advanced features:

Then click on ‘web content filtering’ in settings. If you are doing this for the first time, you have to establish a connection to a third party content category provider called “CYREN“. You can create a 60-days trial with Cyren here. If you have done so, you can then create your first web content filter policy:
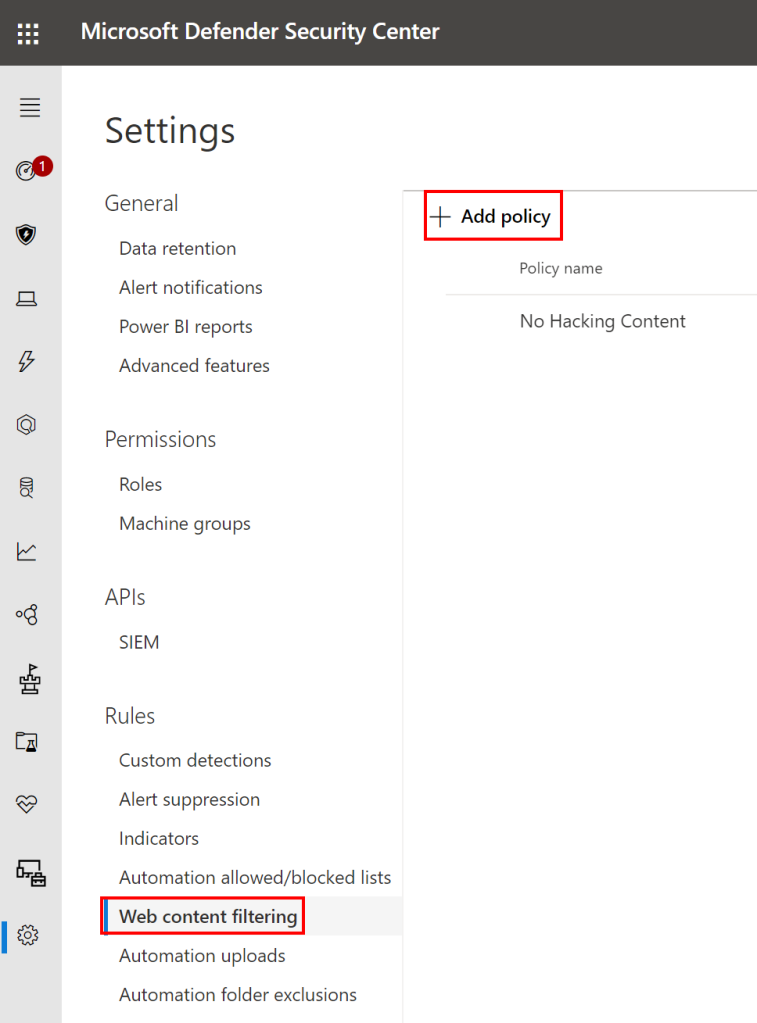
Give it a name:
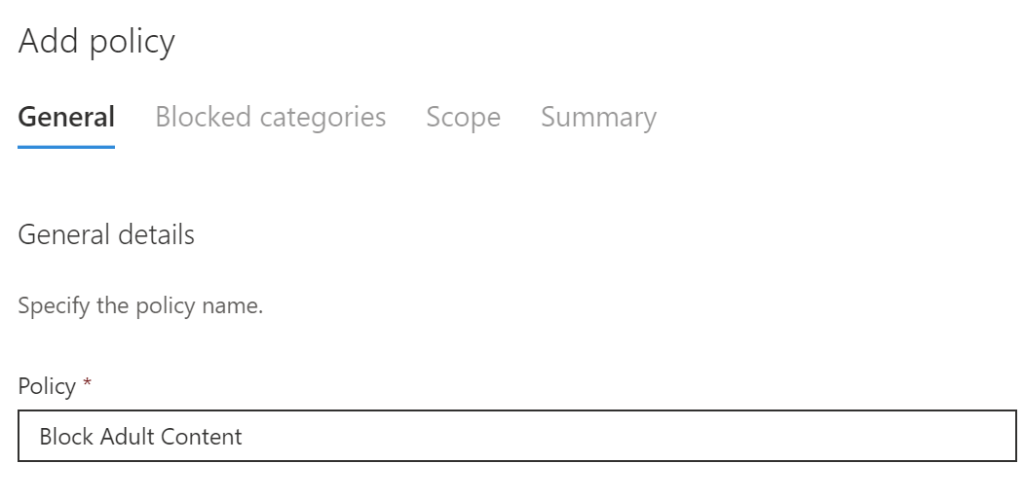
Choose the web content categories you want to block:

As before, specify the scope of your policy:

Now we are set – the configuration part is done. We will look at the user’s perspective in the next chapter. But first a few words on ‘reporting’. In MDATP under ‘Reports\Web protection’ we get this nice overview:

Number 1 and number 3 are based on the same data. Here you get an overview of all indicators: MDATP built-in threat intelligence and custom indicators you configured manually or in MCAS (we will talk about MCAS later).
In the other web-parts (2, 4, 5), you get more information about content filtering. When you click on e.g. a category like “Gambling”, you get more information, like which website triggered the event and how often was it requested by which client:

Blocking based on discovered Apps
Now we switch to MCAS and with that, we switch the perspective. While we were talking about manual blocking of certain domains and content blocking before – we now want to block websites and services based on the apps that were discovered in your environment.
MCAS reports which SaaS services your users are using. It is working hand-in-hand here with the MSsense.exe, the client component of MDATP that actually does the reporting on the client.

The list above is a good report of your (shadow) IT (at least for the SaaS part), you get much more information when you click on one of the apps:
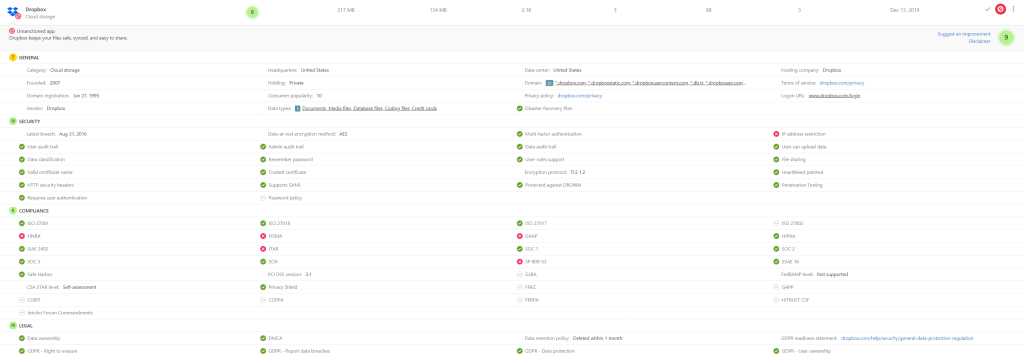
In this picture, you see all the information regarding security, compliance, legal and some general stuff, Microsoft is gathering for you. With that, you can better decide if you want to block it or not.
You also get an overall score and statistical information on how many users are using this service and how many data has been exchanged.
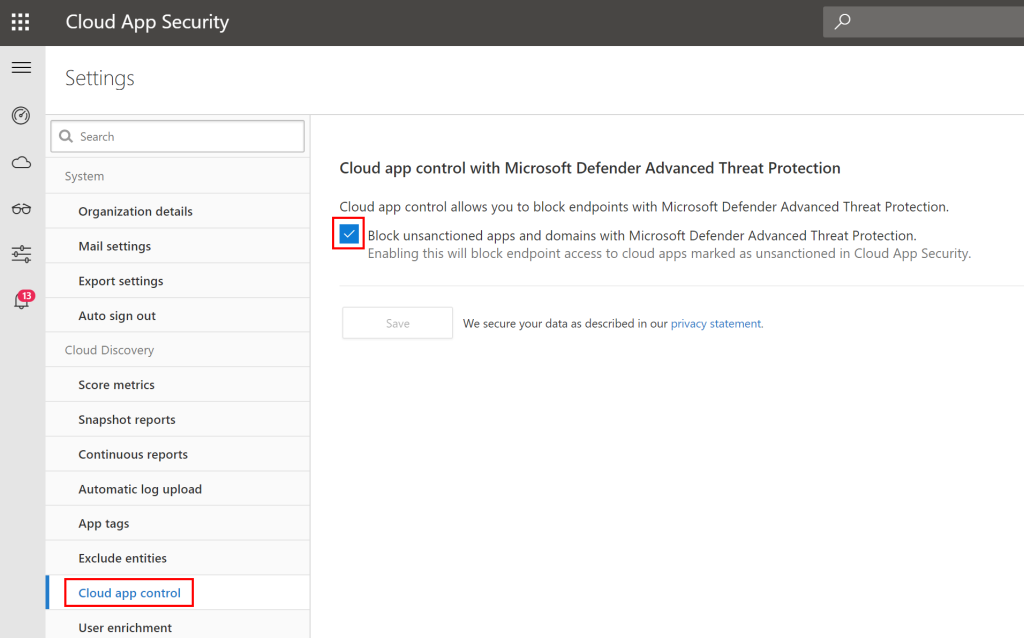
If you have decided to block it – you first must enable this functionality in MCAS/Settings:
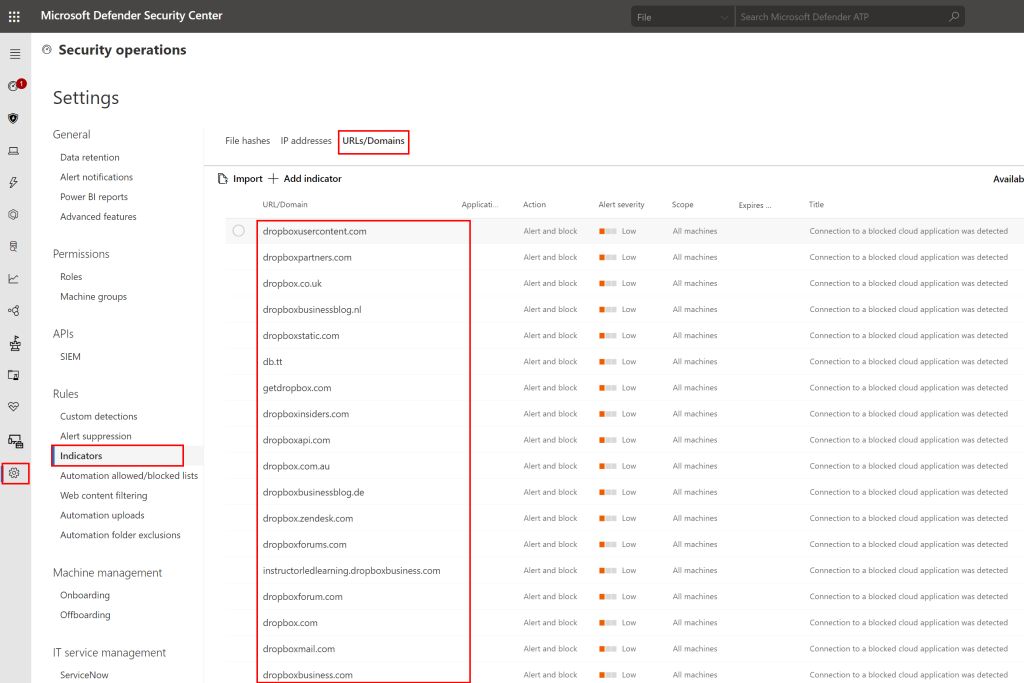
Then, on the very right of the service listing, you can click to block it:

If you do that, the appropriate URLs will automatically be entered into the MDATP indicators list:
In Edge, the user will then get the following message:

And this one here in other browsers:
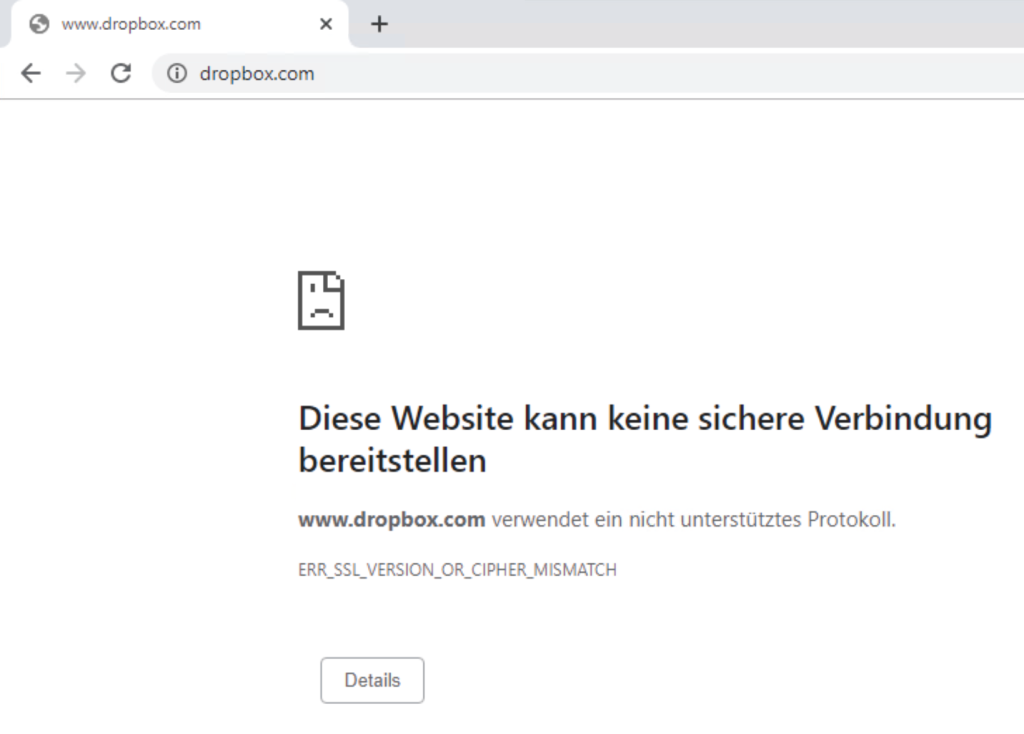
In addition, you get a Windows fly-out:
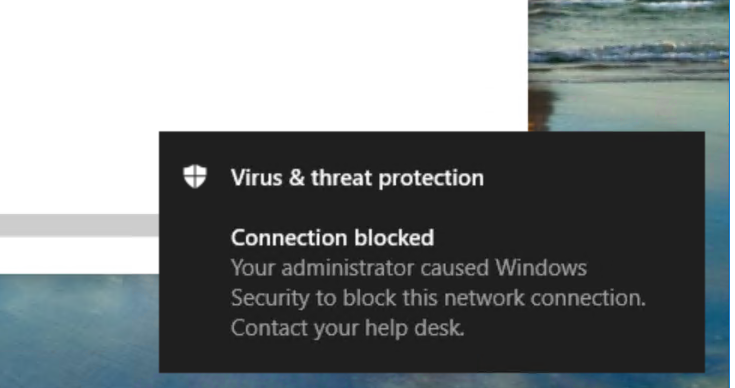
To customize the text of the fly-out check this here.
But not only the browser will be blocked – basically every http(s) traffic – also in the apps:

A PowerShell Invoke-WebRequest does also not work:

To deeper investigate on those events, use queries in MDATP advanced hunting:

Conclusion
Blocking content in a modern workplace scenario is solved. These are good news, since this could have been a blocker 😉 in the past. I think it was solved in the best possible way: on the client and not through a proxy/firewall/filter …!
Do the Catagories also block Proxy services? Otherwise someone could just visit a proxy site and bypass the filter?
LikeLike
Great article Jan! Do you now if MDATP web filtering does SSL inspection?
LikeLike
Thanks! It could, since it sits on the client in the network stack. But here the feed, which URL should be blocked, comes from third party …
LikeLike
I see that websites can be blocked by category. Is there a way to add exceptions to the categories? We have found in the past that we need more granular control than simply blocking sites based on a category. There are sites that we’d like members of staff to access but nothing else from that category.
LikeLike
You can add a domain on a whitelist, yes (indicator of compromise)
LikeLike
Hi
Awesome article.
I have few questions
1. If we make a policy to block certain categories like Adult site or gambling site, did everytime the URL’s fall in this category get blocked generates an alert in ATP?
2. If in case we want to remove any URL that is benign for us but fall in blocked category, can we whitelist it through Cyren side? And if yes then how?
LikeLike
Thanks!
1. there are no default alerts, but you see it in the timeline and via hunting (and in reporting)
2. yes, see a comment above. Through custom IOC whitelisting.
LikeLike
Great article, great features
Unfortunetly, new MDATP for Mac create issues with traffic routed over a vpn connection
LikeLike
Thanks!! Get rid of the VPN 😉
LikeLike
Hello, thank’s you.
Is it possible to block all images and videos on internet ?
LikeLike