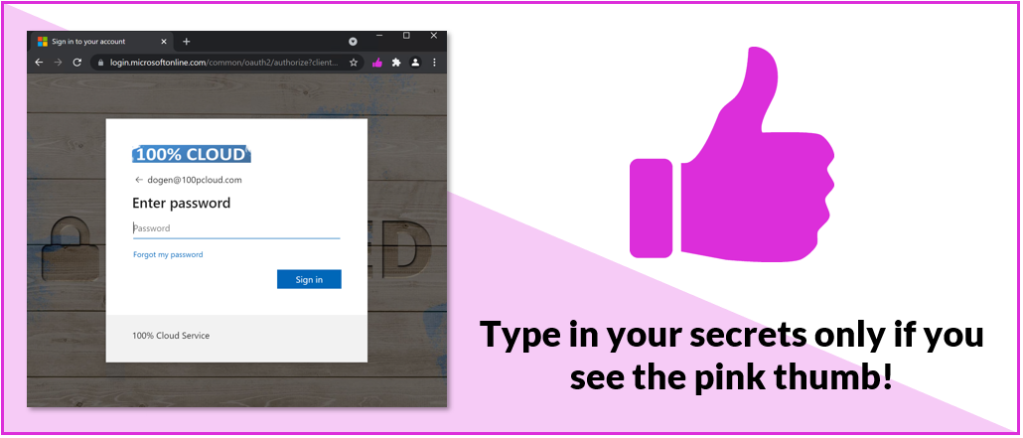
Pink Thumb
That’s gonna be an easy story: people receive phishing mails that contain links. They click on the links and then, they are prompted for their passwords.
To help users (and ourselves) to make better decisions, on which sites to type their passwords and on which not, I have created a very simple chrome extension (that also works on edge): PINKTHUMB – let’s call it a showcase.
Why are people providing passwords or other secrets to phishing sites?
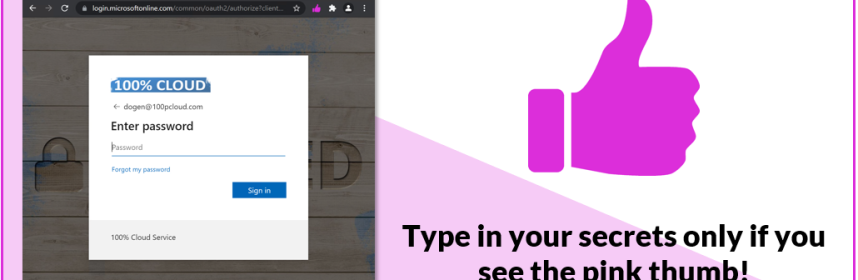
Because the context of the Email and/or the website that prompts for the password convinces them that it is legit. Here is an example:
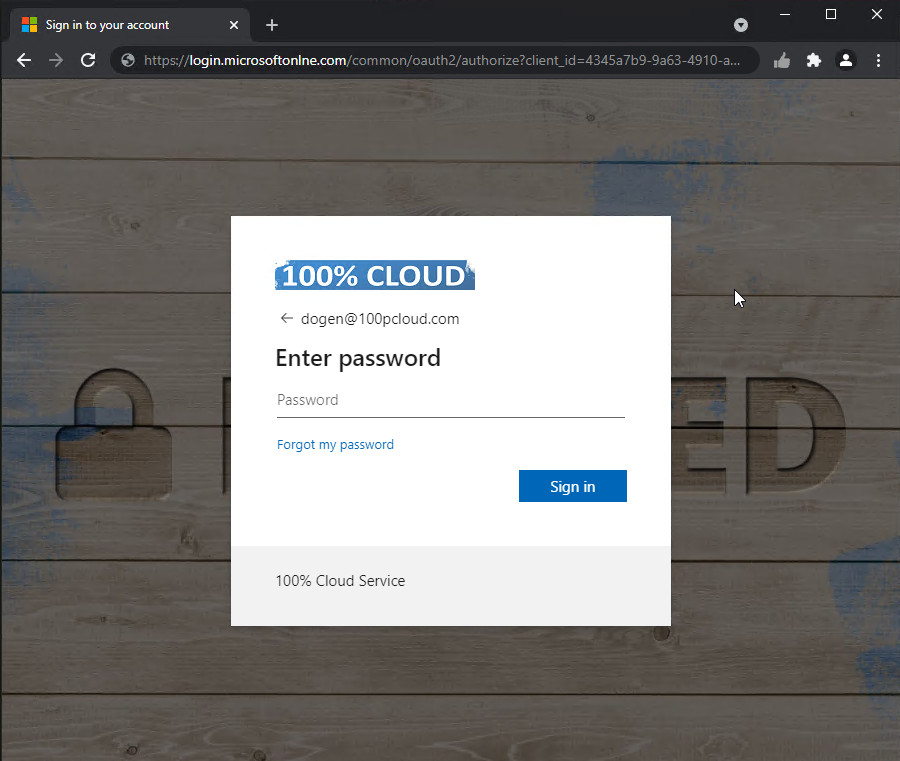
What’s wrong with the above page? Yep, the ‘i’ is missing in ‘online’. That’s why you do not get a pink thumb. You only see it, when the URL finds the correct match in the JSON that holds the configuration for the PINKTHUMB extension:
The JSON file lists URLs that you trust, where typing in your passwords and secrets is fine. The extension then reads all the URLs from this JSON and whenever you browse to such a URL (hostname actually), it displays the pink thumb. You can then teach your users to only type in their secrets, when they see the pink thumb:
Behind the scenes
The most important part of the extension is highlighted below:
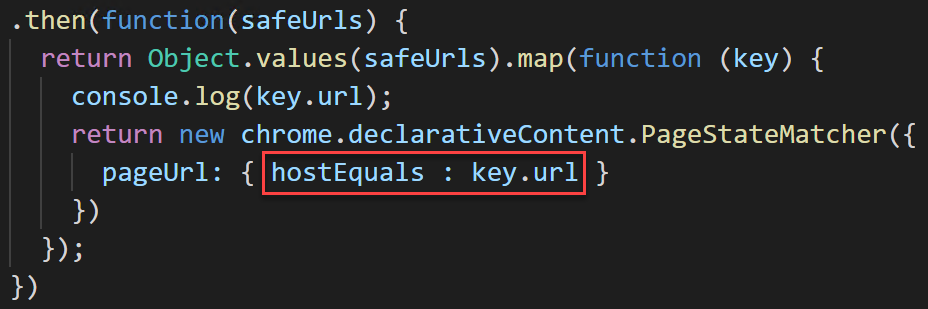
With that filter, we make sure that only hostnames that match our JSON config are treated as trusted (https://developer.chrome.com/docs/extensions/reference/events/#type-UrlFilter). If we would use for example “urlEquals”, something like this would also be valid: phishingsite.com/login.microsoftonline.com/bla
Q & A
Q: But shouldn’t we not rather get rid of passwords at all and get ‘password-less’?
A: yes.
Q: But this will not work for all possible phishing attacks out there, right?
A: yes.
Q: Will this work when I deploy it to all computers in my company?
A: it works on my machine!! No, really, please read the last section of this article!
How to get it / Install
You can install PINKTHUMB from the google store at:
(or manually from my GitHub repository).
Either way, make sure, it is pinned:
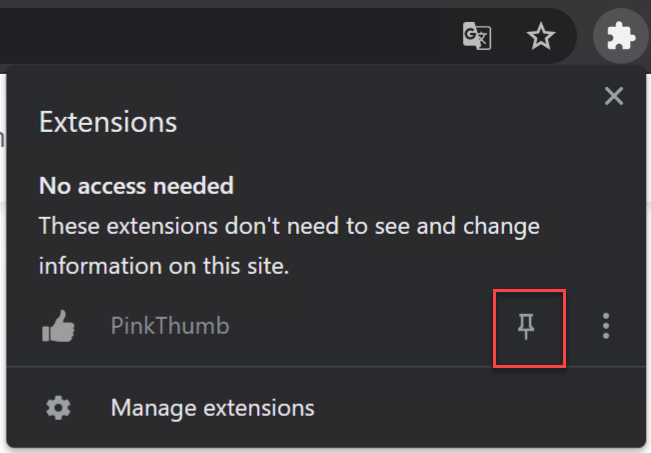
With the above link, you can also add the extension to your chromium based EDGE browser (therefore you need to allow chrome extensions, but you will get an popup for that).
To configure your own URLs, browse to the folder of the extension:
- Chrome: %localappdata%\Google\Chrome\User Data\Default\Extensions\dapfpmoeljjjpmkcnbgbgkkfkpjfigah\1.0_0\config
- Edge: %localappdata%\Microsoft\Edge\User Data\Default\Extensions\dapfpmoeljjjpmkcnbgbgkkfkpjfigah\1.0_0\config
open the urls.json and edit/extend it:
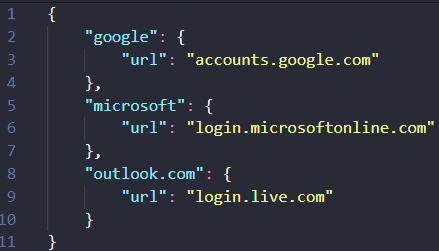
Future Ideas, The Enterprise & Call to Contribute
In general, such a concept should be integrated into the browser(s) and visualize websites that are trusted, even better. It will be not easy for all users to use this extension, as they need to manually edit the JSON file at the moment. This can be improved in the future by providing an OPTIONS file to make the config editable from a GUI. There could be also an option to add the current website to the config – as a trusted site. If you want to contribute here, please let me know or send a PR to my GitHub.
From an Enterprise perspective, to manage the configuration of the extension on the long run, you can distribute the JSON easily to your user’s disks and keep them up to date with whatever you are using to deploy software or configure your clients. However, it would be better – again – to have all this integrated with e.g. Intune (MEM). Did I mention this is just a ‘showcase’?
Writing such extensions is quite easy, I did this over a weekend. However, it is my first extension, and I am not very familiar with javascript (and now I know, I don’t have the desire to get more familiar with it), so don’t blame me for anything related to it – no warranties :). BUT AGAIN: if you see potential here, please feel free to contribute to the project. Thanks!
The main reason why I created this is, because of the idea itself. I think it has the potential to get a feature in the browsers and e.g. in Intune and to close some parts of the gap until we are all password-less.
Pingback: 10 tips to secure your identities in Microsoft 365 - JanBakker.tech
How about wildcard or regex support in the .json file?
e.g. *.yourdomain.com
LikeLiked by 1 person
Pingback: 12 quick tips to secure your identities in Microsoft 365 - Blog - Sonne´s Cloud